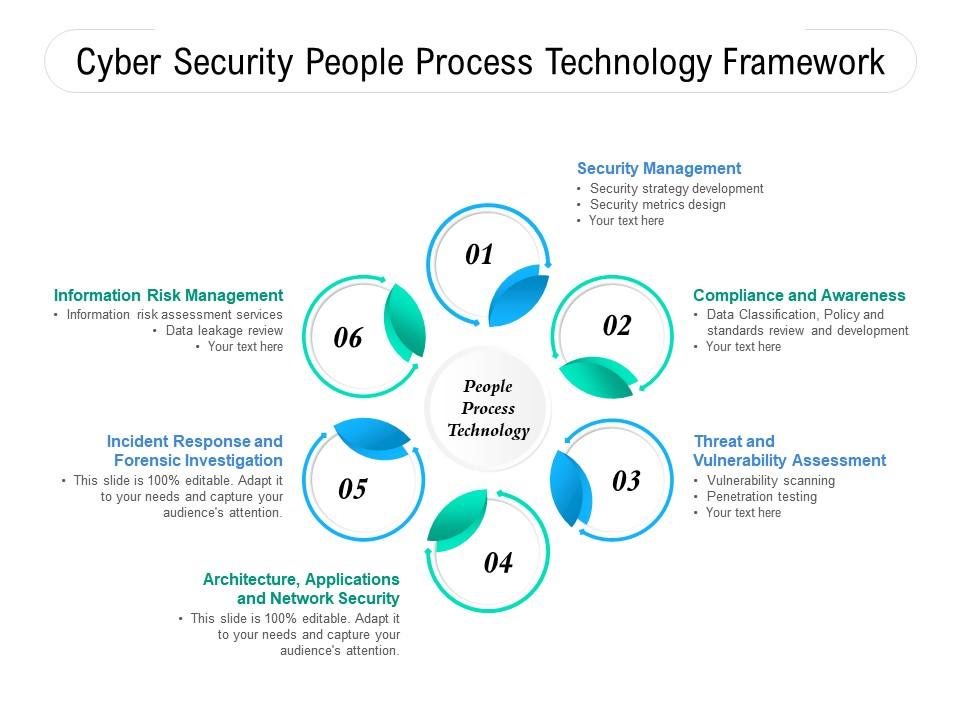
Cyber Security People Process Technology Framework | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas
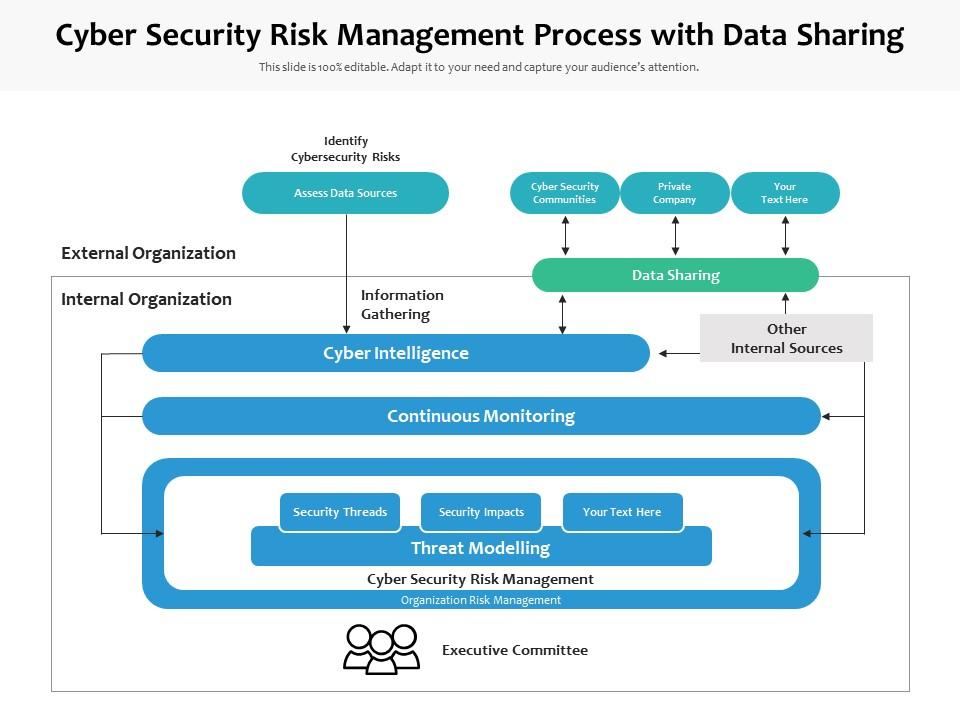
Cyber Security Risk Management Process With Data Sharing | Presentation Graphics | Presentation PowerPoint Example | Slide Templates