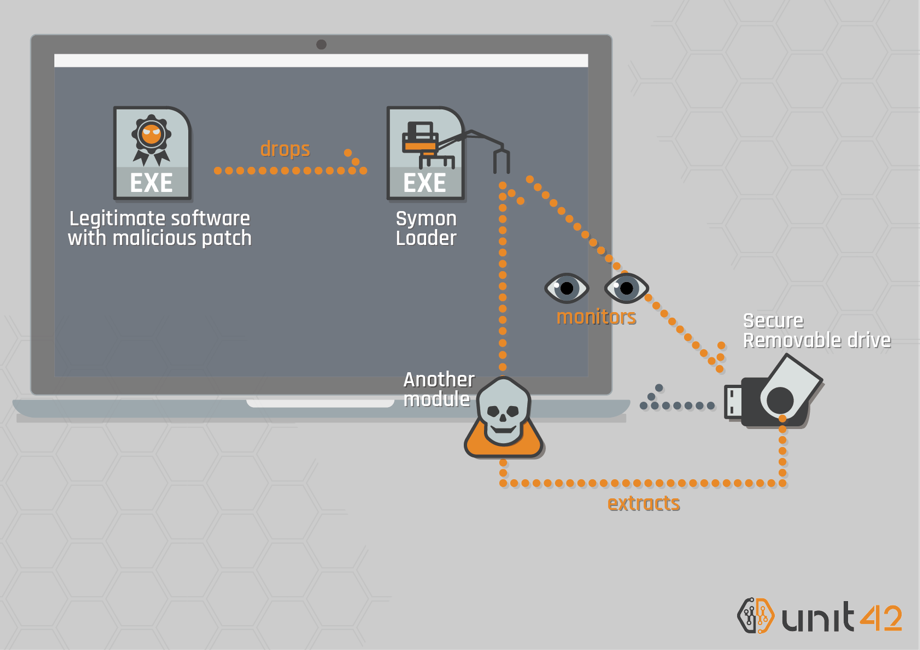
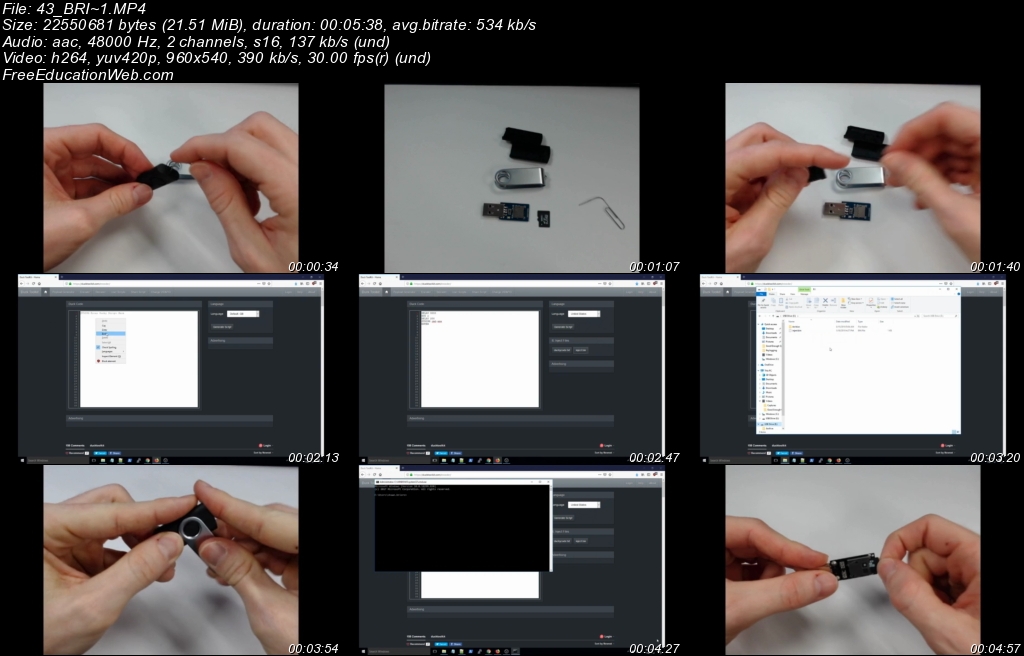
Cybrary - 💻FREE COURSE 📚 "USB Drop Attack" - Discover how attackers disguise attacks to make them successful https://app.cybrary.it/browse/course/usb-drop-attack | Facebook

Kitsap Networking Services, Inc. - USB DROP ATTACK, what do you need to know? There has been numerous threats and hacks that have been conducted in weird and new ways, but what